💀 What Is Ransomware? (Deep Dive):
Ransomware is no longer just a virus — it’s a business model. It’s a calculated, multi-stage attack designed to inflict maximum operational, financial, and psychological damage.
🎯 Technical Definition:
Ransomware is malicious code that encrypts files or systems and demands payment in exchange for a decryption key. It can also exfiltrate data and threaten public exposure, a tactic known as double or triple extortion.
🧬 Types of Ransomware in 2025
- Crypto Ransomware: Encrypts local and networked files using AES-256 or ChaCha20. Example: LockBit 3.0.
- Locker Ransomware: Blocks access to your entire system or apps. Used mainly on mobile and IoT devices.
- Doxware/Extortionware: Steals sensitive data before encryption. Threatens to leak it online or sell it.
- Wiperware Disguised as Ransomware: Poses as ransomware but is actually a destruction tool (used by APTs).
- Mobile Ransomware: Spreads through SMS phishing or malicious Android APKs.
- IoT Ransomware: Locks smart thermostats, security systems, or industrial sensors. Example: ThingLocker.
🔍 Anatomy of an Attack (Expanded Flow):
Let’s break down what a real ransomware attack looks like in 2025.
Phase 1: Initial Entry
- Phishing email with malicious .docx or .iso
- Compromised credentials from the dark web
- Vulnerable software or outdated VPN
🔍 In 2025, over 85% of successful ransomware incidents begin with a human error — someone clicking something they shouldn’t.
Phase 2: Foothold and Privilege Escalation
- Attacker drops tools like Cobalt Strike, Mimikatz, or Rubeus
- Gains domain admin rights or lateral access through Kerberoasting, Pass-the-Hash, or Golden Ticket attacks
Phase 3: Spread
- Malware spreads via PsExec, RDP, or wormable exploits
- Targets backups, file shares, and domain controllers
- Bypasses antivirus using fileless scripting (e.g., PowerShell, WMI)
Phase 4: Encryption + Exfiltration
- Files are encrypted with unique per-system keys
- Data is sent to attacker-controlled servers using tools like MEGAsync, Rclone, or Torrents
- Exfiltrated data includes financials, HR, legal, and trade secrets
Phase 5: Extortion and Negotiation
- Ransom note is dropped (often in every directory)
- Payment portals are hosted on Tor with chatbots for “negotiations”
- Threats include:
- Data leak
- DDoS attack
- PR campaign against you
- Notification to clients or regulators
- Data leak

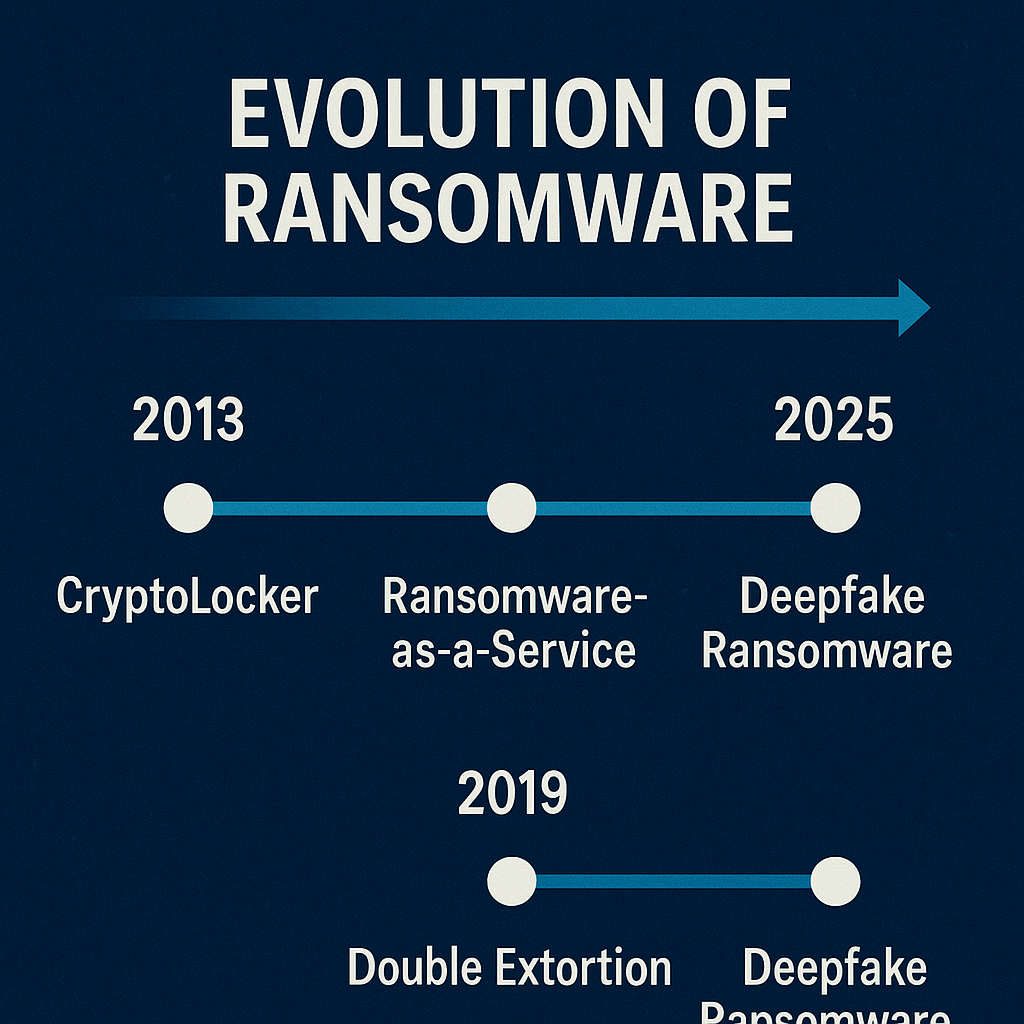
📈 Ransomware Evolution: From Simple to Sophisticated:
Ransomware has evolved from small-scale attacks to corporate-level cybercrime empires.
🧭 Timeline Expansion:
- 2013 (CryptoLocker): The first real “professional” ransomware
- 2016–2017 (Cerber, WannaCry, Petya): Global outbreaks leveraging stolen NSA tools
- 2020 (Maze, REvil): Introduced double extortion
- 2022–2024 (BlackCat, LockBit): Multi-language support, cloud targeting, exfiltration
- 2025 (AI + RaaS): Fully automated, scalable ransomware business models with deepfake, IoT, and crypto obfuscation support
💥 Notable Ransomware Disasters (Expanded):
🏥 NHS & WannaCry (2017)
- Exploited unpatched systems
- Caused ambulance diversions
- Result: >$120M in damages and permanent system overhauls
🛢️ Colonial Pipeline (2021)
- Ransomware disrupted 45% of U.S. East Coast fuel
- Caused panic buying, FAA intervention
- Aftermath: $4.4M paid, later partially recovered by FBI
🏛️ Costa Rica Government (2022)
- Entire government network crippled
- Tax and medical systems down for weeks
- Ransom: $20M, refused
- Declared national emergency
🧬 Henshin Biotech (2024)
- Research data on next-gen CRISPR tools stolen
- Clinical trial sabotage
- Stock price dropped 42% in 3 days
🔥 What’s Different in 2025?
- AI as a weapon: Email lures and scripts are auto-generated, tested, and personalized at scale.
- Deepfake video/audio: Voice clones instructing internal staff to “approve access” or “make payments”.
- Multi-pronged attacks: Encryption + data theft + DDoS + fake press leaks
- Supply chain attacks: Targeting MSPs, vendors, or software updates to reach hundreds of clients at once
🤖 How AI & Deepfake Phishing Changed the Game:
In 2025, phishing isn’t just a typo-ridden email. It’s hyper-personalized psychological warfare.
🧠 Tools Used:
- ChatGPT-like LLMs craft multilingual, company-specific lures
- DeepVoice replicates executive speech patterns
- GAN-generated faces for fake LinkedIn/Zoom accounts
🔍 AI phishing success rates have tripled since 2022 — averaging 78% open rates and 42% click-through.
💣 Real-World Phishing Scenario:
“Hey Dan, here’s the updated quarterly numbers the CEO asked for. Can you forward this to Payroll for verification?”
Includes:
- Real logos
- Correct sender domain (typo-squatted)
- Deepfake attachment: video of CEO “approving” the invoice
📡 IoT Ransomware: The Hidden Threat:
The rise of smart buildings, smart homes, and Industry 4.0 has opened new doors — literally.
🏠 Home Example:
- Smart door lock stuck on “locked”
- Thermostat raises temperature to 95°F
- Mobile alert: “Pay 0.1 BTC to unlock your home”
🏭 Industrial Example:
- Conveyor belts halted mid-run
- Inventory control corrupted
- No physical backup due to digital-only factory management
🧰 Ransomware-as-a-Service (RaaS) Expanded
RaaS platforms are now the Amazon of cybercrime.
🛠️ Inside a RaaS Dashboard:
- Victim tracker with location, company name, sector
- Chat module for ransom negotiations
- Attack builder: Select OS, language, payload type
- Built-in encryption toggles and evasion modes
💰 Some RaaS groups even offer 24/7 tech support and monthly “feature updates.”
📜 Regulation Breakdown
🇺🇸 SEC (USA)
- Must disclose ransomware breaches within 72 hours
- Non-disclosure = shareholder lawsuits + potential jail time under SOX
🇪🇺 EU (NIS2):
- Broadens scope to nearly all “essential entities”
- Requires:
- Incident response drills
- Vendor risk management
- Real-time threat monitoring
- Reporting within 24 hours
🌐 Other Regulations:
- Australia’s Security of Critical Infrastructure Act (2024 Update)
- Singapore’s Cybersecurity Act now includes third-party cloud vendors
- Brazil’s LGPD mandates breach transparency for all sensitive data leaks
🛡️ Cyber Insurance: The Hard Truth
Insurers have learned their lesson — the hard way.
Claims skyrocketed. Payouts ballooned. Premiums soared. Now?
💬 “You want ransomware coverage? Prove you’re worth insuring.”
❌ Denied If:
- No MFA or phishing training logs
- Incomplete asset inventory
- Vulnerable VPNs
- No offline backups
- “Unknown” root cause of incident
🚨 Your 12-Step Survival Plan (Fully Expanded)
- AI Email Filtering: Use LLM-based anomaly detection — not just keyword filters.
- MFA Everywhere: Not just on email — enforce it on GitHub, CRM, backups, internal tools.
- Immutable Backups: Use WORM storage or air-gapped systems.
- EDR & XDR: Detect fileless, lateral movement, zero-day patterns in real-time.
- Patch Faster: Automate via RMM tools; focus on VPNs, RDP, firewalls, firmware.
- Simulated Attacks: Conduct tabletop ransomware drills with PR/legal involvement.
- Kill Macros by Default: Set GPO to block macro-enabled Office files unless whitelisted.
- Network Segmentation: Use VLANs and access control lists to limit blast radius.
- Threat Hunting: Actively scan for indicators of compromise — don’t wait for alerts.
- Secure IoT: Change factory credentials, segment devices, disable cloud access if unnecessary.
- Legal Readiness: Have ransomware clauses in your contracts and IR policy.
- Cyber Insurance Checklist: Audit your own posture quarterly to stay eligible.
🎯 Final Word: You Can’t Afford to Wait
“There are two kinds of companies: those who’ve been hit by ransomware, and those who will be.” — Anonymous CISO
Ransomware in 2025 is not just a script — it’s a weaponized economy fueled by automation, psychological manipulation, and global coordination.
But with the right mix of awareness, policy, tech, and action, you can harden your defenses and stay one step ahead.
This isn’t just cybersecurity — it’s business survival.
🔗 Recommended Tools & Resources for Ransomware Protection
Whether you’re a small business owner, IT admin, or just someone who wants to stay ahead of the curve — these trusted tools and guides will help you build a stronger cybersecurity posture in 2025.
🧩 Internal Resources from Adam Tech Guide
🛡️ Top 10 Cybersecurity Best Practices Everyone Should Follow
Learn how to improve your password hygiene, implement MFA, and avoid common traps like phishing.
👉 Read more
⚙️ WP Rocket vs LiteSpeed Cache: Performance Comparison
Speed matters for security. Find out which caching plugin also helps reduce attack surface on WordPress.
👉 Explore the comparison
🔍 Bluehost vs Cloudways: Hosting Security Face-Off
Not all hosting is created equal. See how these two giants handle malware protection, backups, and traffic filtering.
👉 See the face-off
🌐 External Expert Resources
🔒 CISA’s Ransomware Resource Center
U.S. government-backed hub for ransomware alerts, defenses, and mitigation strategies.
🔗 https://www.cisa.gov/stopransomware
💼 Microsoft Defender for Endpoint
An enterprise-grade endpoint detection and response (EDR) tool, loaded with AI-powered anti-ransomware features.
🔗 Learn more here
📘 NIST Ransomware Risk Management Framework
Recommended reading for IT leaders and compliance teams. Understand the official guidelines for risk reduction.
🔗 https://csrc.nist.gov/publications/detail/itl-bulletin/2021/07/ransomware-risk-management/final
💬 Have I Been Pwned?
Check if your email or company domain has been compromised in past breaches — often a precursor to ransomware targeting.
🔗 https://haveibeenpwned.com/




