You don’t wake up to find “Amazon of cybercrime” trending unless something disruptive is happening.
And that’s exactly what LockBit has become in the world of ransomware — not just a threat, but a model.
It’s a name spoken in cybersecurity circles, incident response teams, law enforcement briefings, and threat reports around the world. So in this post we’re going to go beyond the buzzwords, beyond the headlines, and explain what LockBit really is, why it works, and what it means for every business and website owner in 2026.
We’ll cover:
- The origins of LockBit
- How its business model mimics legal platforms like Amazon
- Why its structure makes ransomware more dangerous
- Real-world examples and attack mechanics
- Practical defense strategies
- How this fits into the larger threat landscape
Along the way, we’ll include links to credible external sources and also connect to related articles you’ll find on Adam Tech Guide, including your cornerstone cybersecurity pieces such as:
Let’s dive in.
The First Time I Heard the Phrase “Amazon of Cybercrime”
Early in my work with security professionals, I came across a report from a threat intelligence provider that used a phrase I hadn’t heard before:
“LockBit operates like the Amazon of cybercrime.”
At first glance it seemed like marketing flair.
But when I read into the details, I realized this was an operational description, not a metaphor.
LockBit had architected its ransomware operations in a way that:
- Delegated execution
- Centralized infrastructure
- Automated revenue sharing
- Rapid iterative improvement
That is not how traditional cybercrime operated. That is how scalable platforms operate.
What LockBit Actually Is
Officially, LockBit is ransomware, meaning malicious software that encrypts data and demands payment to restore access.
But LockBit is more than just malware. It’s a criminal ecosystem.
According to security firm CrowdStrike:
“LockBit is one of the most widespread ransomware families, with affiliates operating worldwide and targeting a broad spectrum of victims.”
👉 Source: CrowdStrike Ransomware Analysis (https://www.crowdstrike.com)
In other words, LockBit’s reach isn’t confined to a single operation or attack — it’s distributed.
LockBit is also notable for being ransomware-as-a-service (RaaS).
That means the core developers don’t necessarily carry out individual attacks. They provide the tools. Others apply them.
According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA):
“Ransomware-as-a-service is a business model that allows affiliates to use ransomware built by developers in exchange for profit sharing.”
👉 Source: CISA Ransomware Guidance (https://www.cisa.gov)
This model dramatically changes the economics of malware.

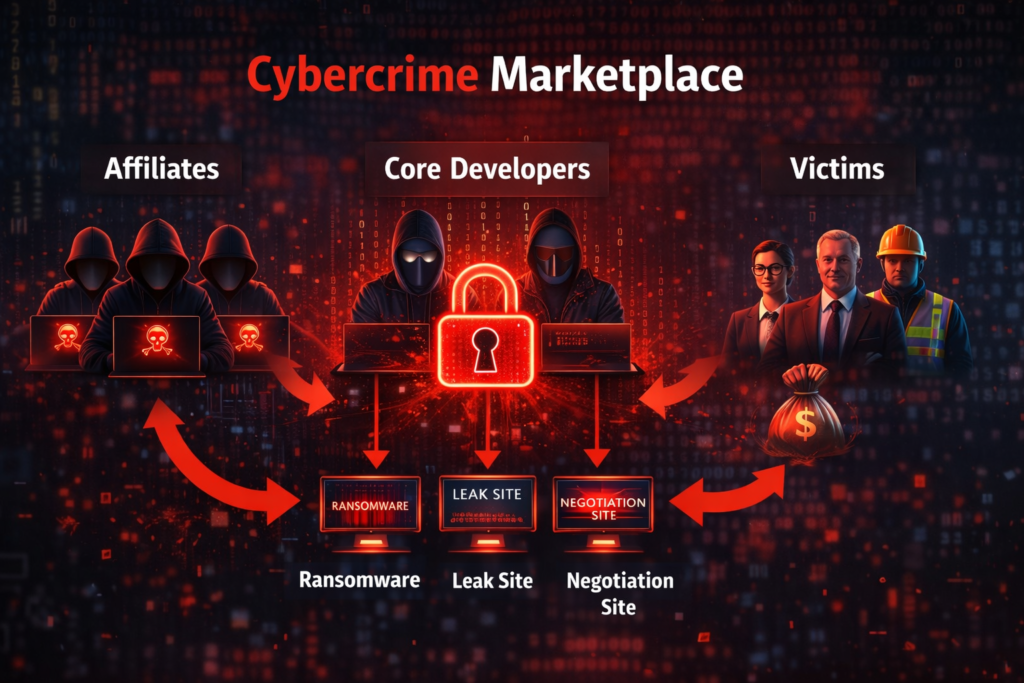
Why the Name “Amazon of Cybercrime” Makes Sense
When people describe LockBit as the “Amazon of cybercrime,” they are referring to the structural similarities, not the ethics.
Amazon is a marketplace. LockBit is a marketplace, too — but for criminal actors.
Here’s how the analogy fits:
🔹 LockBit builds the platform
Develops the ransomware code, management panels, negotiation interface, and support infrastructure.
🔹 Affiliates act as independent operators
They choose targets, launch attacks, and negotiate ransoms.
🔹 Revenue is shared automatically
LockBit takes its cut; affiliates take theirs.
🔹 Competition drives “service quality”
Affiliates seek profitable targets, which drives LockBit to improve usability and features.
This mirrors how legitimate platforms scale and innovate — but in the criminal domain.
This is why some security analysts describe LockBit as industrialized cybercrime.
How Ransomware-as-a-Service Really Works
To understand what makes LockBit special, we need to unpack the RaaS model.
1) Core Developers
LockBit’s core team:
- Writes and maintains the ransomware
- Builds control panels for operators
- Manages leak sites and negotiation systems
They also:
- Offer documentation
- Provide support to affiliates
- Occasionally run bug bounty programs for their own malware
Yes — there are bug bounties in cybercrime.
That alone tells you this is not amateur hour.
External Link (RaaS explanation):
👉 What is Ransomware as a Service? — IBM Security (https://www.ibm.com/topics/ransomware-as-a-service)
2) Affiliates
Affiliates:
- Obtain access to LockBit’s platform (often for a cut of profits)
- Run campaigns
- Choose targets
- Deploy ransomware
LockBit’s platform automates much of the heavy lifting:
- Encryption
- Negotiation portals
- Data exfiltration tools
- Decryption key delivery (if ransoms are paid)
This automation is a big shift from old ransomware — which was often manually operated and inconsistent.
LockBit’s Technical Evolution and Variants
LockBit did not stay static. It evolved rapidly.
Security firm Palo Alto Networks documented multiple versions of LockBit that became more sophisticated over time.
👉 Source: LockBit 2.0 Ransomware Analysis (https://unit42.paloaltonetworks.com/lockbit-2-ransomware)
These evolutions included:
- Faster encryption routines
- Improved evasion of detection
- Multi-platform targets (Windows, Linux, ESXi)
- Data exfiltration coupled with encryption (double extortion)
Each iteration made LockBit more scalable and dangerous.
Double Extortion: LockBit’s Psychological Edge
In the early days of ransomware, attackers only encrypted files and demanded payment.
Today, LockBit and similar groups add double extortion:
- Encrypt your data
- Threaten to release it publicly if you refuse to pay
This not only disrupts operations — it threatens reputation, compliance, and trust.
External link explaining double extortion:
👉 What Is Double Extortion Ransomware?
This psychological pressure often works even if the victim has backups. The fear of public data leaks pushes many to pay.
How LockBit Attacks Typically Start
Despite the sophistication of the LockBit platform, most attacks still begin with simple access methods:
- Exploiting unpatched software
- Compromised credentials
- RDP exposure
- Phishing and social engineering
👉 If you’d like a foundational understanding of social engineering tactics like phishing, check out: 🎣 Phishing in Cybersecurity: The Ultimate 2025 Guide for Beginners.
Once initial access is gained, attackers:
- Escalate privileges
- Move laterally within networks
- Disable security controls
- Execute LockBit ransomware
- Publish stolen data if ransom isn’t paid
This sequence shows why basic security hygiene (patching, MFA, least privilege) matters — topics explored further in 🔐 Top 10 Cybersecurity Best Practices Everyone Should Follow (2025 Edition).
Who LockBit Targets
LockBit does not discriminate by industry, size, or geography.
Victims have included:
- Healthcare providers
- Municipal governments
- Educational institutions
- Manufacturing companies
- Small to medium businesses
According to several cybersecurity reports, LockBit was responsible for a large share of ransomware incidents globally, which highlights just how prolific it became before takedowns.
This breadth of targets underscores that every organization with an online footprint is at risk, not just giants with deep pockets.
LockBit and WordPress: A Tangible Threat for Website Owners
For readers focused on websites (especially CMS-based sites like WordPress), LockBit’s model is especially relevant.
Common WordPress vulnerabilities that pave the way for ransomware include:
- Outdated plugins
- Vulnerable themes
- Weak administrative credentials
- No multi-factor authentication
Once attackers gain a toehold, they may leverage server access to deploy ransomware across backups and databases.
This highlights the importance of proactive defense — a theme you explore deeply in Cybersecurity in 2025 — The Ultimate Guide to Digital Safety, Privacy, and AI-Driven Threats.
The Law Enforcement Response — Did It Work?
In 2024, a major operation called Operation Cronos saw international law enforcement seize LockBit infrastructure and leak sites.
👉 Source: Global Initiative Against Transnational Crime — LockBit Takedown (https://globalinitiative.net)
They also obtained some decryption keys and disrupted parts of the operation.
Yet, despite these actions, LockBit variants — and its conceptual successors — continued to circulate. Affiliates rebranded, new forks emerged, and the ecosystem adapted.
This reflects a truth about modern cybercrime:
Disrupting infrastructure doesn’t eliminate the demand or the economic incentives.
LockBit’s Legacy: A New Era of Cybercrime
LockBit did not merely cause damage — it changed how ransomware is organized, conceptualized, and monetized.
Key takeaways:
- Ransomware now operates like a platform
- Crime marketplaces recruit and train operators
- Automation and scalability have supplanted ad-hoc attacks
- Psychological extortion is now a standard component
In many ways, LockBit’s model set the standard for modern ransomware — which means understanding it isn’t optional. It’s essential.
For broader context on the shifting threat landscape and AI-mediated attacks, see Cybersecurity in 2025 — The Ultimate Guide to Digital Safety, Privacy, and AI-Driven Threats.
Defending Against LockBit and RaaS Threats
Here’s where the lessons become practical.
LockBit attacks exploit poor hygiene, not magic. The fundamentals matter more than ever:
🛡 1. Patch Everything
Software that isn’t patched is an open door.
🔐 2. Strong Authentication
Enable multi-factor authentication everywhere.
📚 3. Least Privilege Access
Limit permissions to what’s necessary.
💾 4. Immutable, Offline Backups
LockBit targets backups first.
👩🏫 5. Human Awareness
Phishing and social engineering are still the ingress vectors.
These are the core principles also reinforced in your Top 10 Cybersecurity Best Practices (2025 Edition) piece.
Final Thoughts — Security Is a Continuous Process
LockBit’s notoriety comes not from malware alone — but from its organizational innovation, one that mimics legitimate platforms in structure and economic incentives.
That’s why the “Amazon of cybercrime” label isn’t hyperbole.
It’s a description of design.
As defenders, we don’t have the luxury of ignoring how adversaries evolve. We must match or exceed that evolution with education, systems, process, and vigilance.
Which is exactly what Adam Tech Guide exists to help you do.
About the Author
Adam is an electrical power engineer, educator, and software developer with real-world experience in automation, IoT, and cybersecurity. He founded Adam Tech Guide to share reliable, hands-on insights about AI, software tools, and modern technology — helping readers make informed, confident tech decisions.





Pingback: Cybersecurity in 2025 — The Ultimate Guide to Digital Safety, Privacy, and AI-Driven Threats - Adam Tech Guide
Pingback: 🛡️ Ransomware in 2025: The Ultimate Survival Guide - Adam Tech Guide